F5 Waf Vs Asm
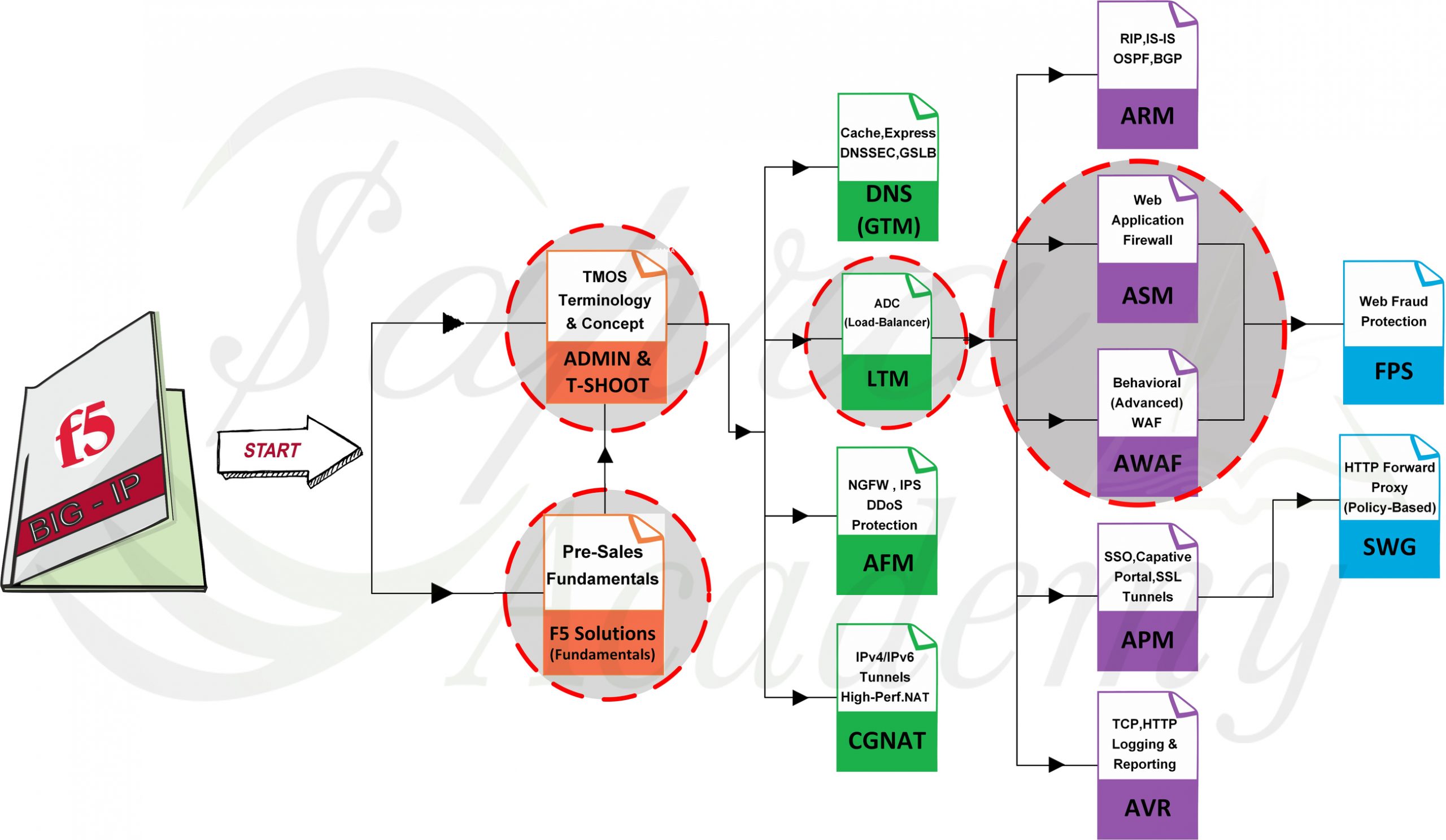
T wo years ago, I studied for 101 Application Delivery Fundamentals and 1 TMOS Administration I passed the exams with an score of 86 and 73 respectively This is the entry level certification for F5 BIGIP Once I got the F5CA certification, I could register for F5 Certified Technology Specialists (F5CTS) certification where I could choose between LTM, DNS, ASM or APM.

F5 waf vs asm. Due to limitations in F5 BIG IP ASM, OPSWAT Deep CDR will not provide the expected results MetaDefender ICAP Server provides the sanitized files back to BIG IP ASM, but these sanitized files are ignored by ASM If the request is allowed, then the original content is released by ASM. F5 Networks Inc BIGIP Appliances run the Application Security Manager (ASM) WAF As of TMOS software version 111 (112 is the latest), the ASM WAF is IPv6capable and provides IPv6 web. F5 WAF solutions including Application Security Manager (ASM), Silverline WAF and Silverline WAF Express protect applications across environments Gartner does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other.
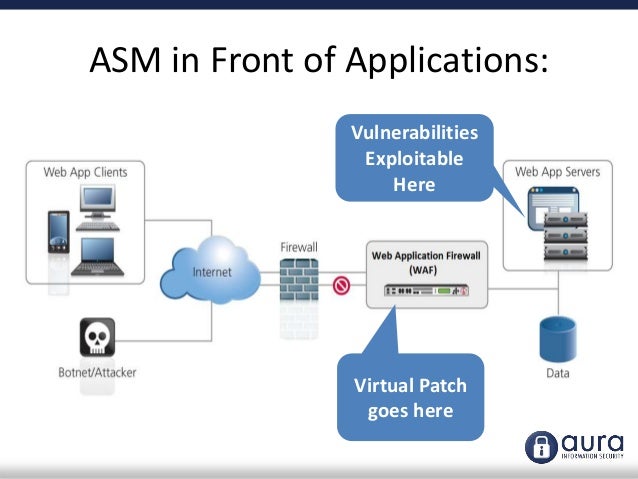
Product Overview The F5 Web Application Firewall solution is delivered by F5's industryleading BIGIP Application Security Manager (ASM) and BIGIP Local Traffic Manager (LTM), providing advanced firewall capabilities by securing applications from layer 7 DDoS attacks, malicious bot traffic, common application vulnerabilities and all OWASP top 10 threats. F5 Firewall – Understanding all firewalls of the BIGIP platform Many of us first discovered F5 ® because of their flagship LTM ® & GTM ™ products, but more recently the F5 firewalls have been making waves, namely their Web Application Firewall (WAF) aka the Application Security Manager ™ (ASM ® ) Now, in conversation when you tell people you work with F5, more often than not they say “oh yeah the WAF company!”. Picus Labs discovered that the “rev” and “printf” commands incorporated with command substitution bypass certain attack signature checks of F5 Advanced WAF / ASM / NGINX App Protect products We use this combination of commands in a command execution payload that creates a reverse shell to the target web server.
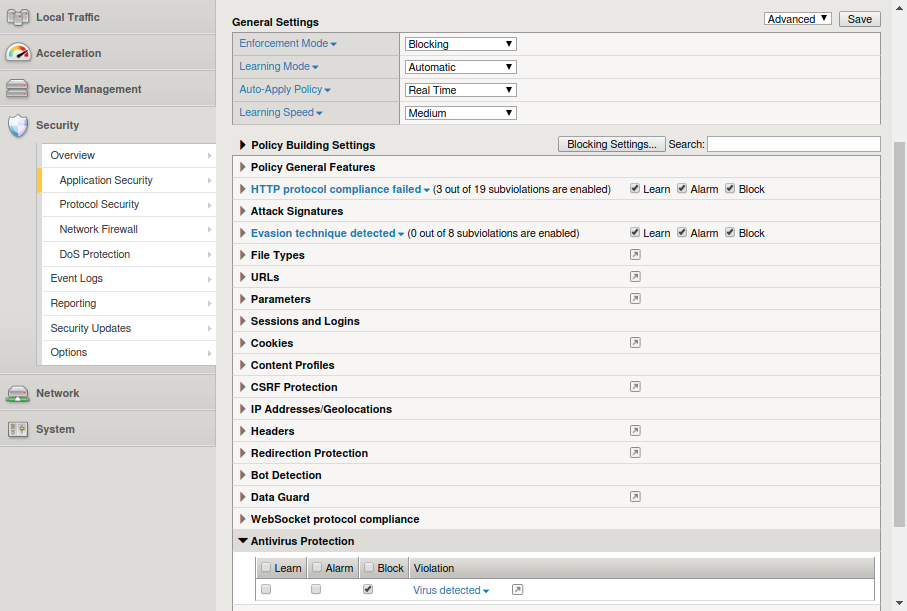
Define a web application firewall;. The F5 Advanced Web Application Firewall (WAF) provides a powerful set of security features that will keep your Web Applications safe from attack Many WAFs. Activate F5 product registration key Ihealth BIGIP ASM 1215, 1214, 1213, 1212, 1211, 1210 Table of Contents > Configuring What Happens if a Request is Blocked Overview Configuring what happens if a request is blocked The Application Security Manager™ has a default blocking response.
Looking at the best Web application firewalls in the market today, there are so many types available that a company is pretty much guaranteed to find a WAF product or service that fits its needs. F5waftester F5 Networks Advanced WAF tester tool to ensure basic security level Overview F5 Networks Threat Research Team has created a tool that provides an easy and fast way to integrate security testing as part of the SDLC process for basic application protection health check before moving to production. Learn F5 ASM (Web Application Firewall) with experts The course includes lecture, handson labs, and discussion about different ASM components Rating 40 out of 5 40 (19 ratings) 2,926 students Created by NetMinion Solutions English English Auto What you'll learn Course content.
Whenever ASM processes a request with a violation, it triggers an ASM_REQUEST_VIOLATION event F5 recommends that you rewrite the iRules using ASM_REQUEST_DONE in the Normal Mode Click Save to save your settings To put the security policy changes into effect immediately, click Apply. Activate F5 product registration key Ihealth ASM™ automatically creates a local traffic policy when you create a security policy or attach a security policy to a virtual server (manually) pool The web server or application server resources that host the web application being protected with a security policy You can create a local. F5 Application Security Module (ASM) and Advanced Web Application Firewall (AWAF) secure web applications against unknown vulnerabilities, enable compliance with key regulatory mandates and protect applications from malicious and abusive bot traffic Successful deployment of these solutions requires a cycle of policy development that minimizes false positives, while still maintaining an.
F5 AntiBot Mobile SDK extends bot identification in Advanced Web Application Firewall (Advanced WAF) and BIGIP ASM protection to allow mobile applications to identify as valid applications, which eliminates bot threats To use this enhanced capability, you must integrate the F5 AntiBot Mobile SDK with your mobile applications. FullProxy’s Adrian Clarke and Donald Ross talk about the Open Web Application Security Project’s top ten security risks #8 is about Insecure Deserialization and how F5’s Application Security Manager (ASM) can help keep your business and data safe from attackers. F5 Advanced Web Application Firewall F5 is one of the more well respected names in the network performance world, with some serious offerings in the high availability/load balancing space.
Configuring BIGIP ASM Application Security Manager (WAF) Course Description In this course, students are provided with a functional understanding of how to deploy, tune, and operate ASM to protect their web applications from HTTPbased attacks. With leading DAST integration and virtual patching, F5 WAF can identify and automatically patch new application vulnerabilities as, or if they arise To reduce application time to market, this solution includes a selection of outofthe box security policies which have been configured by F5 experts, as well as a rapid policy builder to speed up. F5 Advanced WAF Analysts, product testers and users all rate F5 highly Forrester and Gartner rate F5 as a leader, and Gartner says it is one of the most frequently cited vendors in WAF appliance.
Looking at the best Web application firewalls in the market today, there are so many types available that a company is pretty much guaranteed to find a WAF product or service that fits its needs. Why would a customer purchase Advanced WAF instead of ASM?. Advanced WAF has unlimited Behavioral DoS support, and is the platform for future security enhancements such as Credential Stuffing DB, Threat Campaign, C Device ID subscriptions, and automated signaling to F5 Silverline Deployment Scenarios How is F5 Advanced WAF deployed?.
What is a Web Application Firewall?. F5 Networks Arrow is wereldwijd één van de marktleiders in het verzorgen van IT trainingen Meer informatie over onze cursus voor een opleiding in Nederland Configuring F5 Advanced WAF (previously licensed as ASM) v151. F5 BIGIP Application Security Manager (ASM) Integration Web Application Firewalls (WAFs) are critical in the implementation of a robust application security strategy Ideally placed to break the upstream web stream of web servers (in ReverseProxy), WAFs can analyze the contents of HTTP requests and responses to a new level of granularity with respect to an IPS or IDS.
ELK stands for elasticsearch, logstash, and kibana Logstash receives logs from the F5 WAF, normalizes them and stores them in the elasticsearch index. Learn F5 ASM (Web Application Firewall) with experts The course includes lecture, handson labs, and discussion about different ASM components Rating 40 out of 5 40 (19 ratings) 2,926 students Created by NetMinion Solutions English English Auto What you'll learn Course content. Community Training Classes & Labs > F5 Web Application Firewall Solutions > Lab 22 Session Hijacking Protection Session hijacking is a class of attacks that allow an illegitimate user to take control of a legitimate session that was initiated by a legitimate user.
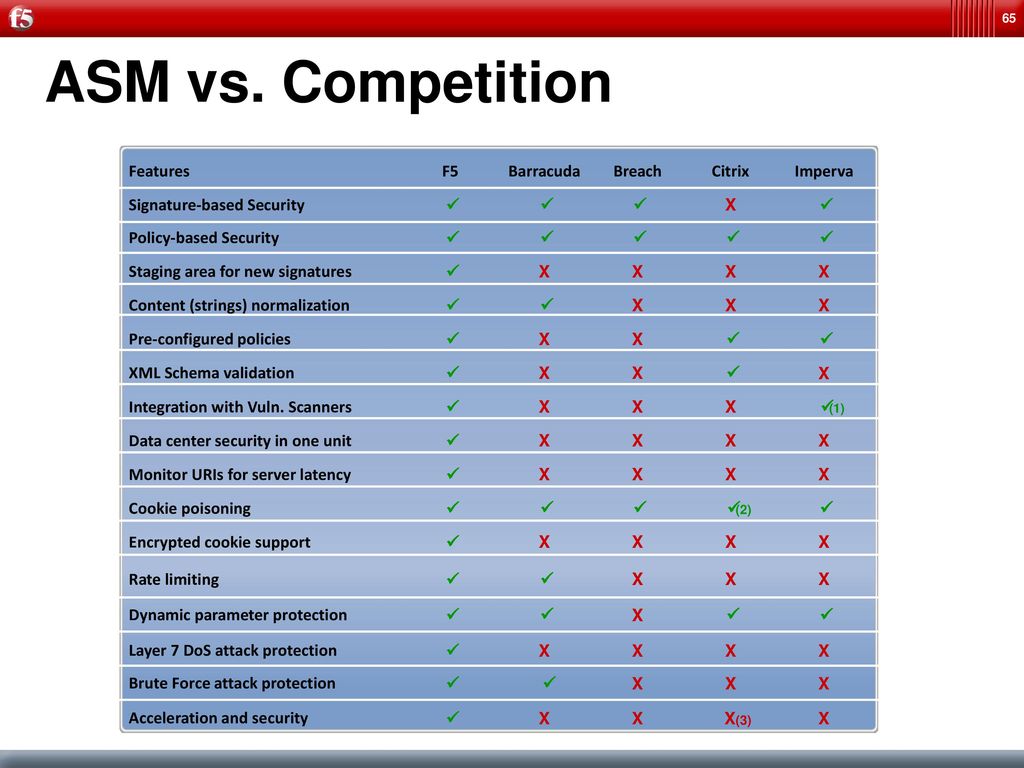
A software or hardware solution that protects your web enabled applications from threats/attacks The solution must understand web protection at the application layer (HTTP and HTTPS conversations to your web applications, XML/SOAP, and Web Services) Detect/prevent OWASP Top Ten Threats. F5 BIGIP Application Security Manager (ASM) Integration Web Application Firewalls (WAFs) are critical in the implementation of a robust application security strategy Ideally placed to break the upstream web stream of web servers (in ReverseProxy), WAFs can analyze the contents of HTTP requests and responses to a new level of granularity with respect to an IPS or IDS. F5 Advanced WAF is ranked 5th in Web Application Firewall (WAF) with 16 reviews while Microsoft Azure Application Gateway is ranked 4th in Web Application Firewall (WAF) with 9 reviews F5 Advanced WAF is rated 86, while Microsoft Azure Application Gateway is rated 76 The top reviewer of F5 Advanced WAF writes "It is very stable as as a load balancer or a web application firewall".
Configuring BIGIP ASM Application Security Manager (WAF) Course Description In this course, students are provided with a functional understanding of how to deploy, tune, and operate ASM to protect their web applications from HTTPbased attacks. The course includes lecture, handson labs, and discussion about different ASM components In this course we will be discussing below topics Application Traffic Flow Initial setup of BIGIP Basic traffic processing components on F5 HTTP header and explanation of OWASP Top 10 Security Model Ways to deploy initial security policy on ASM. John Wagnon covers the different policy types available for building out an application policy on F5 BIGIP ASM.
Describe how F5 Advanced Web Application Firewall protects a web application by securing file types, URLs, and parameters. Configuring the F5 BIG IP Appliance The following configuration steps should be done from the F5 BIG IP Management Console interface The steps below describe the minimum configuration required for MetaDefender ICAP Server integration with F5 BIG IP Please refer to Configuring BIGIP ASM antivirus protection for a more advanced configuration. Application Security Manager (ASM) This is F5’s Web Application Firewall (WAF), if you understand how traditional firewalls block and allow traffic by means of IP & Ports, you can think of the F5 ASM as filtering and protecting everything after the slash “/” in your URL – specifically on the contents of requests to your web application, including the URIs and posted parameters.
Provision F5 Advanced Web Application Firewall resources;. Objectives Describe the role of the BIGIP system as a full proxy device in an application delivery network;. ELK based dashboards for F5 WAFs This is community supported repo providing ELK based dashboards for F5 WAFs How does it work?.
In this 4 day course, students are provided with a functional understanding of how to deploy, tune, and operate F5 Advanced Web Application Firewall to protect their web applica Configuring F5 Advanced WAF (previously licensed as ASM) v151 (TPF5N_BIGAWFCFG). F5 Advanced WAF management interface is now webbased and purposebuilt for security practitioners so the policy configuration, logging, alerting, violation severity and analysis are all there as. Hi respected members, I need your suggestions to get the following features from WAF (Web Application Firewall) I have no idea about that which solution will provide these features 1) Bruteforce attack detection 2)Wrong password and username.
What is a Web Application Firewall?. F5 Security Partner of the Year 19 Read more Close FullProxy Main Nav Solutions Solutions submenu App Security Web Application Firewall Cloud Security. The focus of an F5 Web Application Firewall is the protection of internal (custom) web applications from external threats within the application layer SecureLink is a highly specialized security integrator, our best practice is to implement the F5 Networks WAF and Palo Alto Networks NGFW technology in a serial way within the internet access.
Maybe not directly an F5 use case is that if you have an IDS system in combination with an F5, you can get messages into ArcSight that there is a case of Mac address spoofing (eg MAC flip/flop), because the F5 is handling traffic on different physical VIP interfaces with the same IP address You can filter out these events in ArcSight. F5 WAF solutions including Application Security Manager (ASM), Silverline WAF and Silverline WAF Express protect applications across environments Gartner does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other. Community Training Classes & Labs > F5 Web Application Firewall Solutions > Lab 22 Session Hijacking Protection Session hijacking is a class of attacks that allow an illegitimate user to take control of a legitimate session that was initiated by a legitimate user.
F5 BIGIP ASM 1141 Filter Bypass Posted May 6, 15 Authored by Peter Lapp The F5 ASM is a web application firewall designed to protect web applications from attacks Due to the way that the system processes JSON content, it's possible to bypass the ASM using a crafted request to a URL that processes both JSON and regular URL encoded requests. Advanced WAF (AWAF), which enables customers to benefit from an expanded feature set, replaces the BIGIP ASM F5 ® has quietly grown into the leader of web application firewalls with their Application Security Manager ™ (ASM ®) module and their Advanced Web Application Firewall (AWAF) AWAF extends F5’s WAF with new features to combat fraudulent credential stuffing & bot mitigation, along with a whole slew of other new features. F5 Networks Inc BIGIP Appliances run the Application Security Manager (ASM) WAF As of TMOS software version 111 (112 is the latest), the ASM WAF is IPv6capable and provides IPv6 web.
Advanced Web Application Firewall (WAF) Protect your apps with behavioral analytics, proactive bot defense, and applicationlayer encryption of sensitive data Use the ROI Estimator from F5 and Forrester to find out how Advanced WAF can improve your security posture and save you money. FullProxy’s Adrian Clarke and Donald Ross talk about the Open Web Application Security Project’s top ten security risks #8 is about Insecure Deserialization and how F5’s Application Security Manager (ASM) can help keep your business and data safe from attackers. F5's auto scaling WAF solution employs BIGIP ASM and BIGIP LTM to provide advanced firewall protection, securing your applications against layer 7 DDoS attacks, malicious bot traffic and other common application vulnerabilities while offering powerful reporting and automated learning capabilities Linux/Unix.
Picus Labs discovered that the “rev” and “printf” commands incorporated with command substitution bypass certain attack signature checks of F5 Advanced WAF / ASM / NGINX App Protect products We use this combination of commands in a command execution payload that creates a reverse shell to the target web server. A software or hardware solution that protects your web enabled applications from threats/attacks The solution must understand web protection at the application layer (HTTP and HTTPS conversations to your web applications, XML/SOAP, and Web Services) Detect/prevent OWASP Top Ten Threats. F5 Rules for AWS WAF Web exploits OWASP Rules Sold by F5 Networks Protect against web exploits F5 Web Exploits Rules for AWS WAF, provides protection against web attacks that are part of the OWASP Top 10, such as SQLi, XSS, command injection, NoSQLi injection, path traversal, and predictable resource.
5 F5 BIGIP Application Security Manager (ASM) Last but not least is the F5 BIGIP ASM appliance You might know F5 as one of Citrix’s primary competitors They’re wellknown for their topnotch load balancers This is an appliance which targets larger businesses. F5 Advanced WAF (AWAF) is a combination of BIGIP ASM, L7 DDoS protection, and a selection of core BIGIP LTM features Therefore, F5 AWAF is much more than F5 ASM because we’ll have more L7 DDoS protection and lots of features of the LTM module It has also more load balancing methods than ASM, and profiles persistence are included, which are not included in ASM. In this 4 day course, students are provided with a functional understanding of how to deploy, tune, and operate F5 Advanced Web Application Firewall to protect their web applica Configuring F5 Advanced WAF (previously licensed as ASM) v151 (TPF5N_BIGAWFCFG).
F5 Rules for AWS WAF Web exploits OWASP Rules Sold by F5 Networks Protect against web exploits F5 Web Exploits Rules for AWS WAF, provides protection against web attacks that are part of the OWASP Top 10, such as SQLi, XSS, command injection, NoSQLi injection, path traversal, and predictable resource.
Redshield Managed Application Security Services Powered By F5 Asm
Individual Vendor Review F5 Red Button

F5 Networks Introduction To Silverline Waf Web Application Firewall
F5 Waf Vs Asm のギャラリー
F5 Web Application Security Ppt Download
Azure And F5 Waf In The Cloud Devcentral

Complete Web Application Firewall Guide By Rezaduty Devconnected Devops Sysadmins Engineering Medium

5 Facts To Know About F5 Big Ip Asm Application Security Manager Uninets Blog
Solutions Admin T Shoot Ltm Asm Awaf ساپرا اکادمی

F5 Networks Configuring Big Ip Advanced Waf V14 Web Application Firewall Formerly Asm Max Technical Training

David Romero Trejo Comparing F5 Advanced Waf And Big Ip Asm

Article K Big Ip Asm Operations Guide Chapter 1 Guide Introduction And Contents
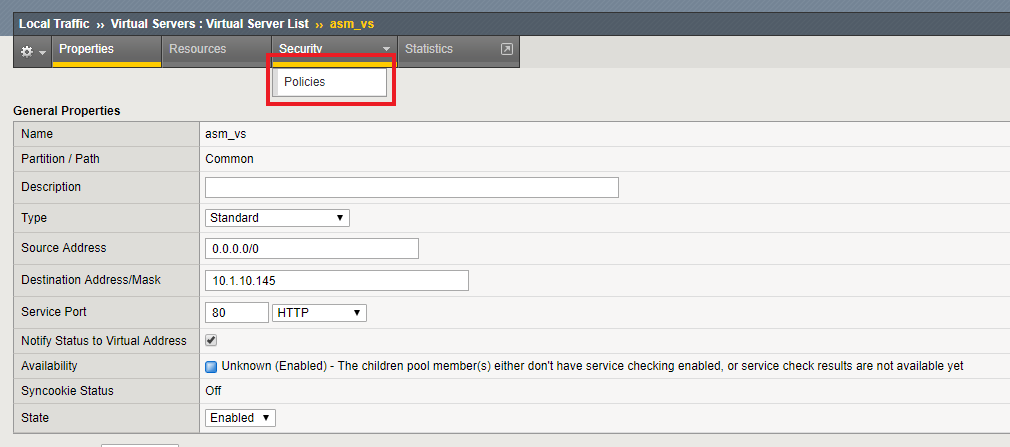
Lab 1 1 Allowed Url List

Seguridad De La Informacion Redes Por David Romero Trejo

Pedro Haoa Cissp F5 Cse Linkedin

Credential Stuffing Prevention With F5 Asm Brute Force Protection The Load Balancer Crew Blog

F5 Networks Big Ip Application Security Manager Appdeliveryworks Com
The Big Ip Application Security Manager Part 1 What Is The Asm Devcentral

F5 Silverline Web Application Firewall Onboarding Technical Note Pdf Free Download
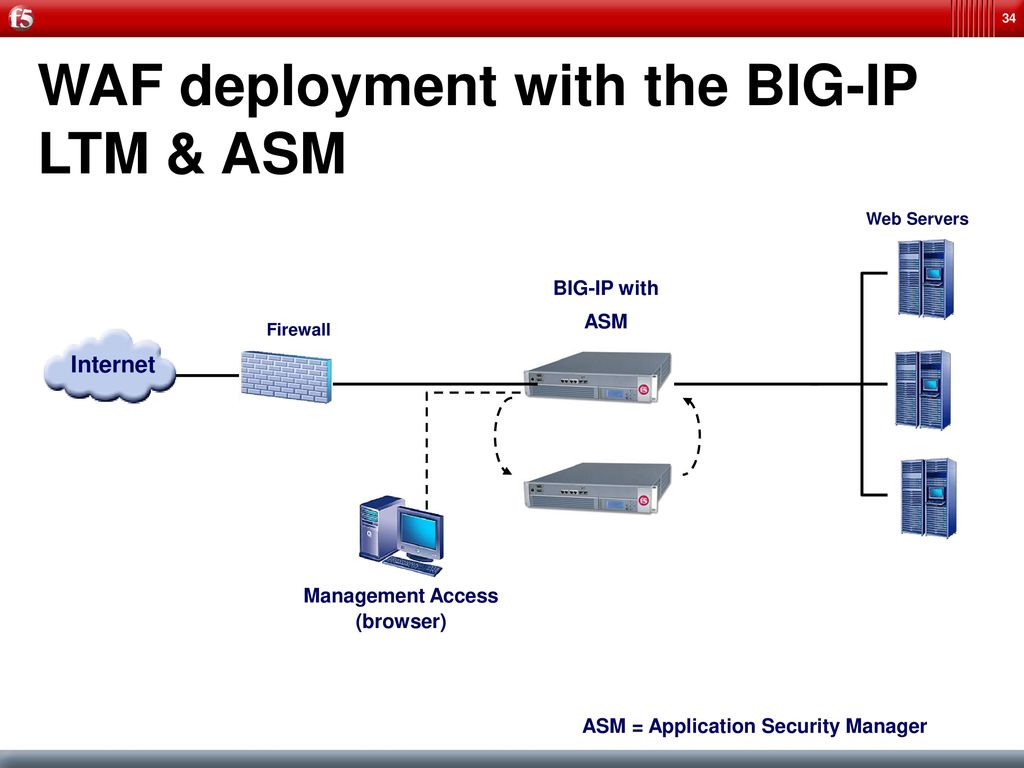
F5 Web Application Security Ppt Download

Article K What Is A Waf

Complete Web Application Firewall Guide By Rezaduty Devconnected Devops Sysadmins Engineering Medium

Ppt Web Application Security With The Application Security Manager Asm Powerpoint Presentation Id
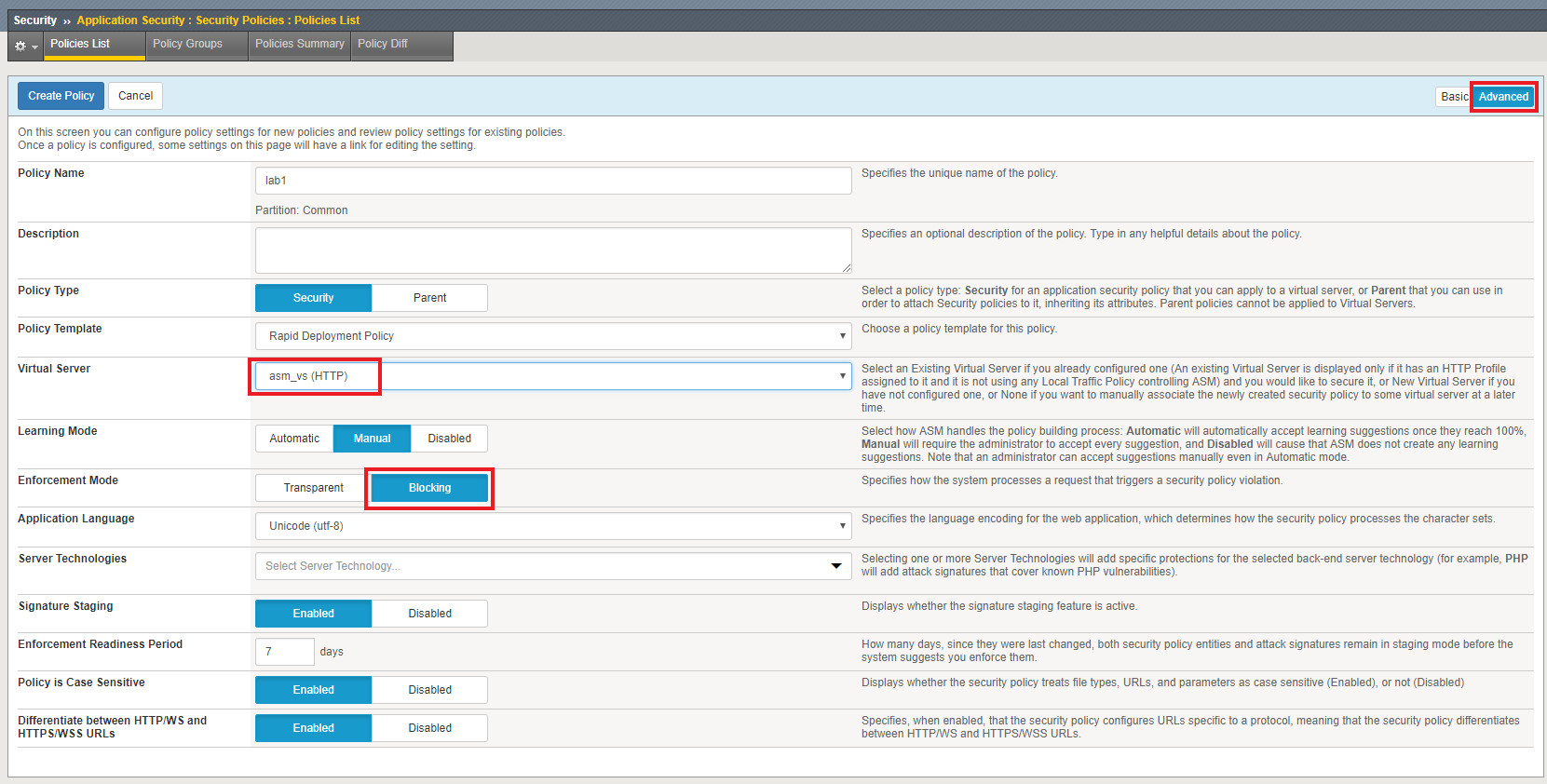
Lab 1 1 Allowed Url List
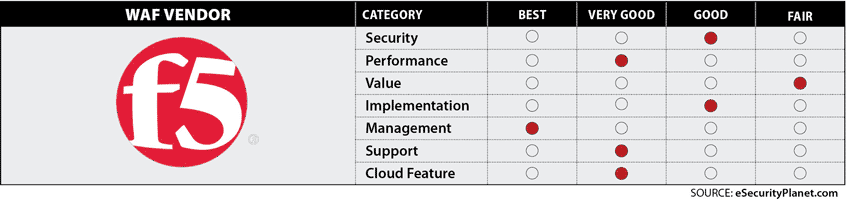
F5 Advanced Waf Esecurity Planet

Article K What Is A Waf

Individual Vendor Review F5 Red Button

Configuring F5 Advanced Waf Previously Licensed As Asm Exclusive Networks Middle East

David Romero Trejo Comparing F5 Advanced Waf And Big Ip Asm

F5 Intro

F5 Waf Security Splunkbase

Owasp Penetration Testing Versus F5 Web Application Firewall Dos Cyber Security Penetration Test Malware Analysis

F5 Big Ip Asm Waf Rules Report Netsparker

F5 Bigip Name Based Reverse Proxy Ltm Policies Somoit Net

Seguridad De La Informacion Redes Por David Romero Trejo
Askf5 Manual Chapter Working With Passive Monitoring

Big Ip F5 Asm Training In India Aplearnings
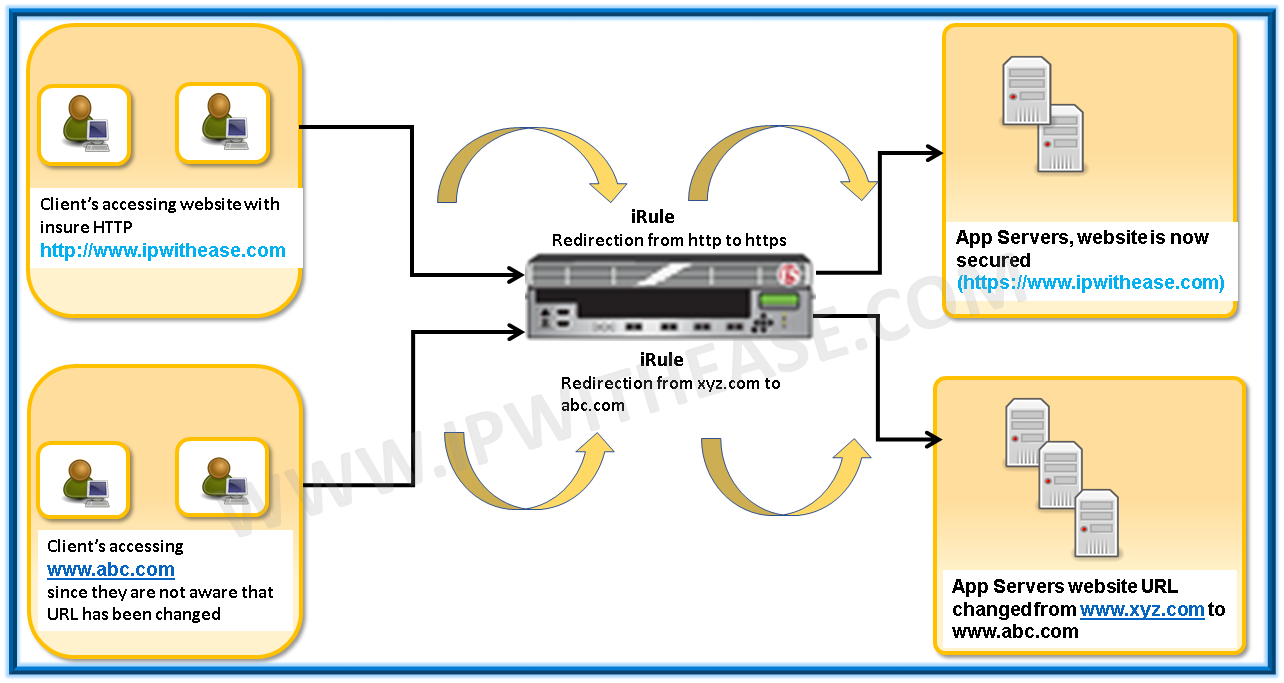
Irule In F5 Big Ip Ip With Ease
Silverline Waf Architecture Devcentral

F5 Bigip Asm Waf Nettech Cloud
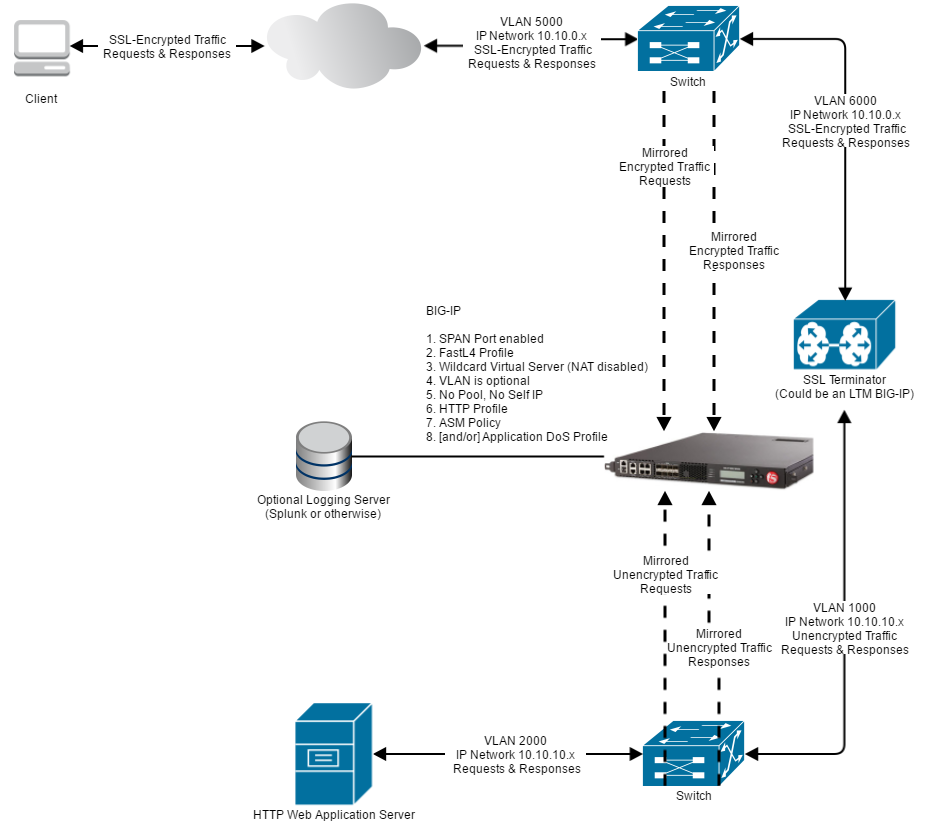
F5 Big Ip Asm Waf Metadefender Icap Server

F5 Certification Costs How To Become F5 Certified F5 Exams

F5 Big Ip Reviews And Pricing It Central Station

Waf Vs Ngfw

Article K What Is A Waf

F5 Awaf Vs Asm What S The Difference Between F5 S Asm And Awaf Worldtech It

Setting Up And Tuning F5 Asm Waf Policy With Dvwa Enforcement 2 Youtube

F5 Awaf Shape Layered Security Is The Best Security Worldtech It

Aws Api Gateway Protection With Big Ip Youtube

10 Best Web Application Firewalls Waf Vendors Reviewed In 21

Article K What Is A Waf

Introduction To Asm Dedicated To My Non Persian Languages Friends

F5 Awaf Shape Layered Security Is The Best Security Worldtech It
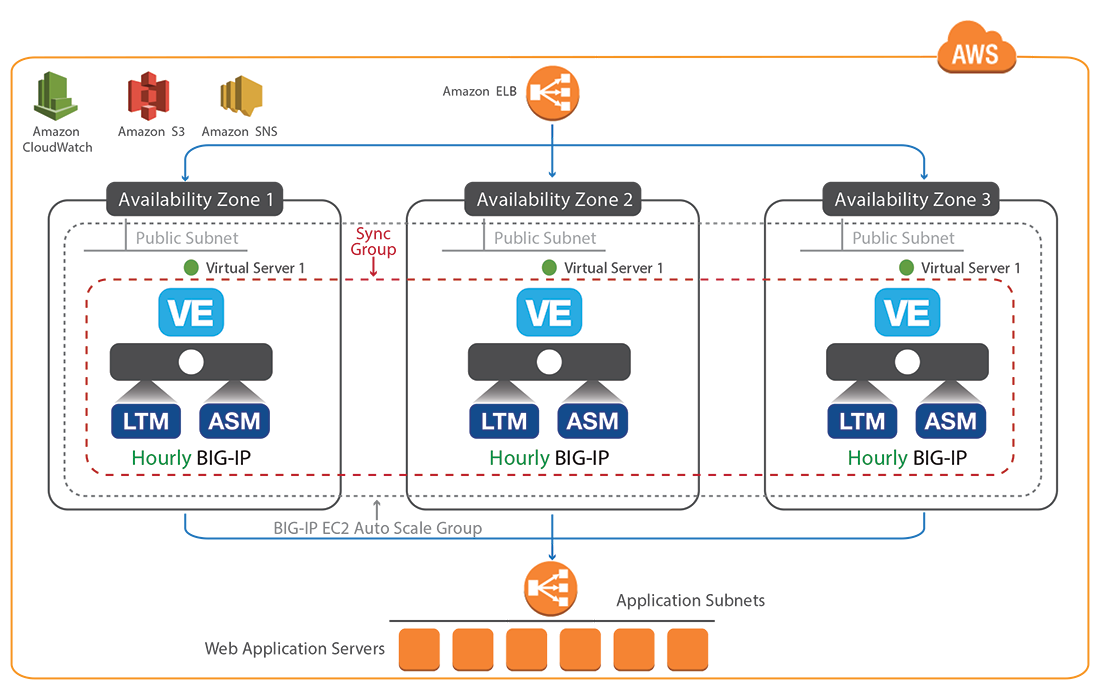
How F5 S Waf Earned Its Aws Security Competency

Pbc Asm Adv Waf Full Course Workbook V13 1 B Pdf Big Ip Asm Adv Waf Partner Edition Participant And Hands On Exercise Guide Document Version Course Hero
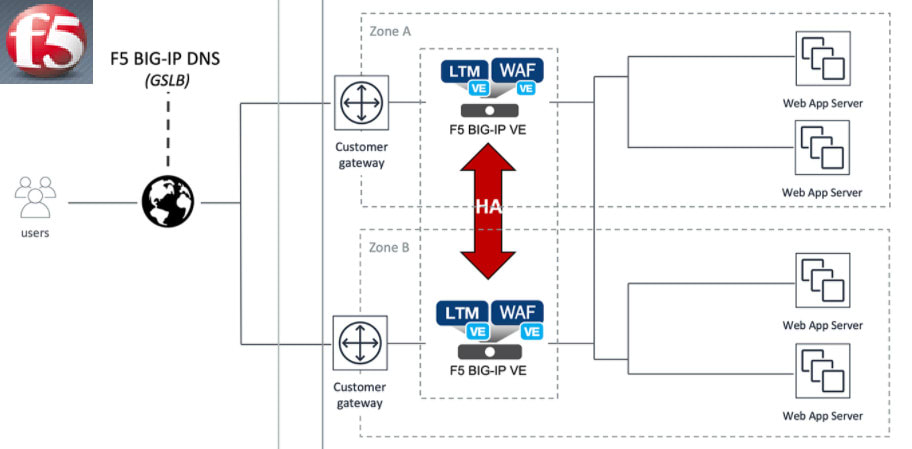
F5 Ltm Dns Asm Design Configure And Tshoot By Mubashirfarooq

Simplicity And Security Through Centralized Application Delivery And F5 Networks Aws Partner Network Apn Blog

F5 Big Ip Application Security Manager Asm

F5 Awaf Vs Asm What S The Difference Between F5 S Asm And Awaf Worldtech It
Bots Mitigations Overview With Advance Waf Anti Bot Engine Devcentral

2 2 1 Lab 2 Deploy An F5 Web Application Firewall Using The Azure Security Center Azure F5 Lab Days Documentation

Nexum Configuring F5 Advanced Waf Previously Licensed As Asm V14

F5 Big Ip Asm Waf Rules Report Netsparker

Advanced Troubleshooting Working With Violations On Asm F5 Waf Web Application Firewall Youtube
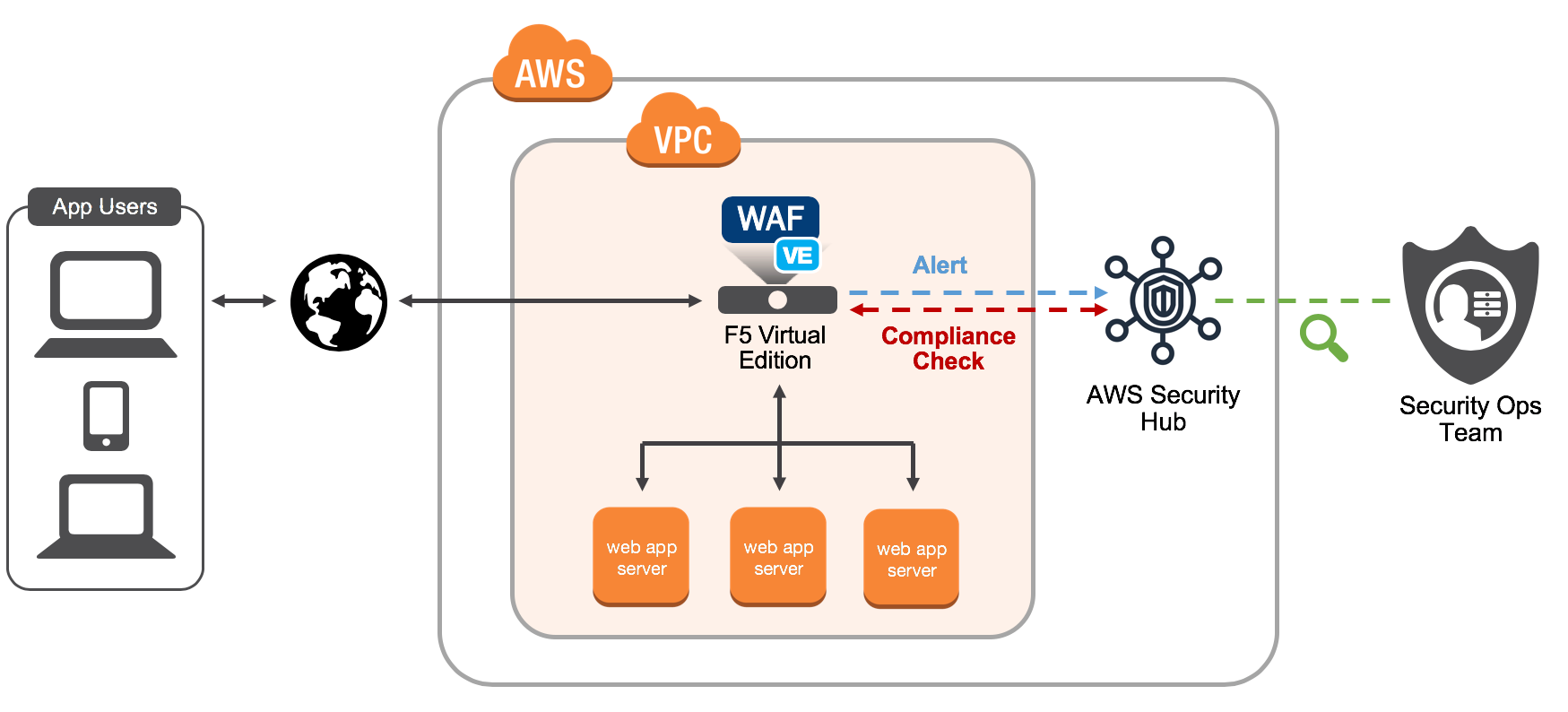
F5 Waf Support For Aws Security Hub Empowering Centralized Security Reporting
Import Scan Results Into F5 Big Ip Asm Acunetix

Lab 1 4 Protection From Parameter Exploits

Key Considerations For Application Security F5 Advanced Waf Vs Asm
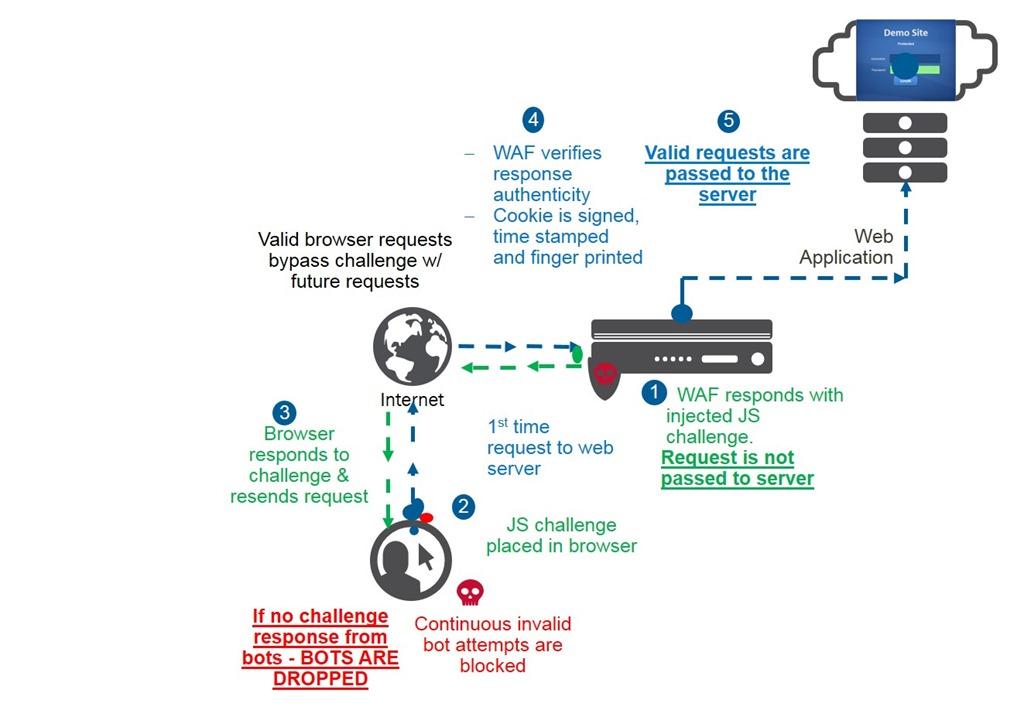
F5 Devcentral Proactive Bot Defense Using Big Ip Asm By Johnwagnon T Co Fy9irgfkio Bigip Security

Aws Marketplace Web Application Firewall

F5 Awaf Vs Asm What S The Difference Between F5 S Asm And Awaf Worldtech It
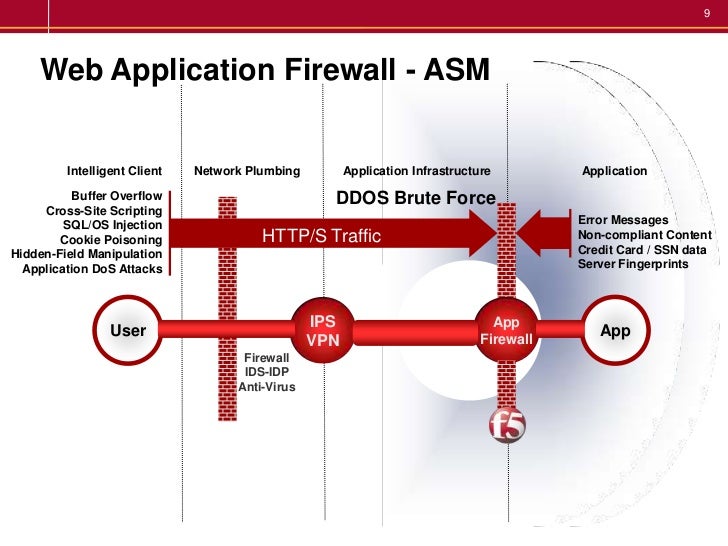
F5 Bigip Asm Introduction
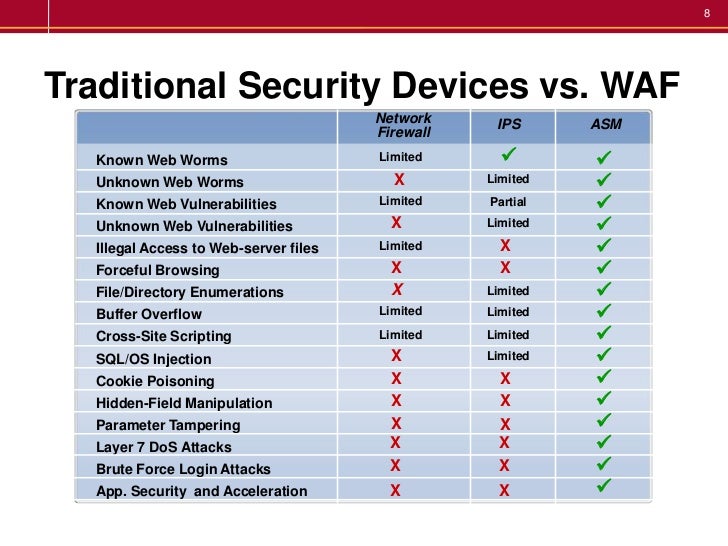
F5 Bigip Asm Introduction
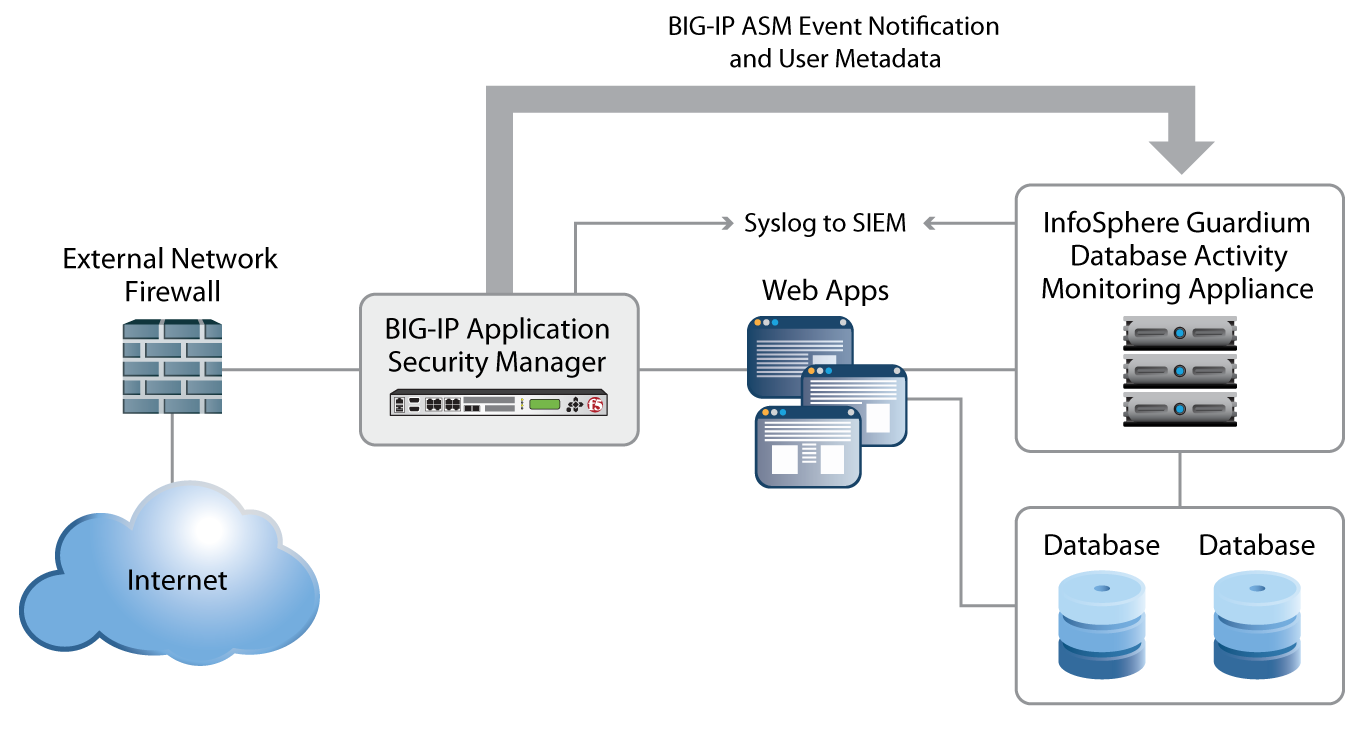
Application And Database Security With F5 Big Ip Asm And Ibm Infosphere Guardium
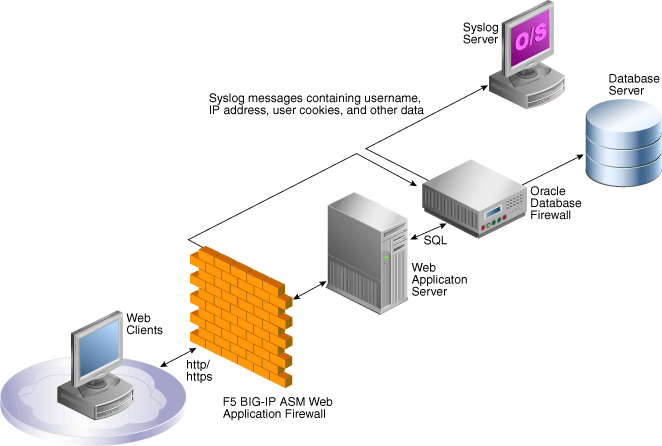
Using Oracle Database Firewall With Big Ip Asm

F5 Bigip Asm Introduction

Web Application Firewall Waf Security Solution Falco Solution
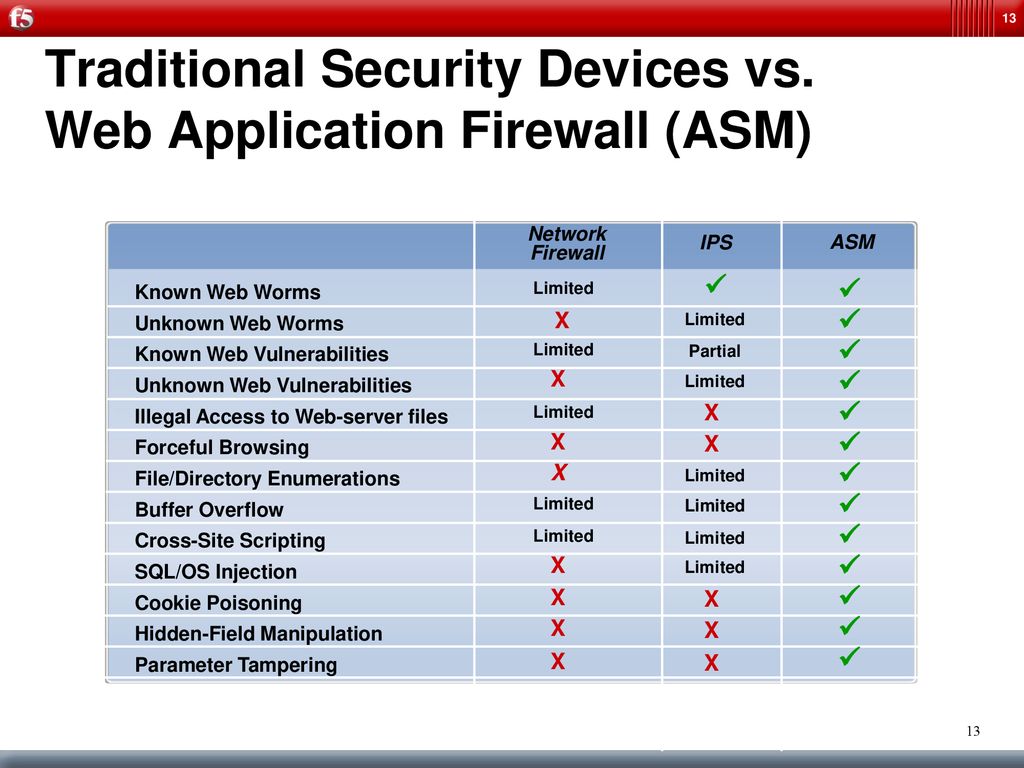
Web Application Security With The Application Security Manager Asm Ppt Download

4 Open Source Web Application Firewall For Better Security
Exercise 2 1 Protocol Compliance

100 Off Learn F5 Asm Web Application Firewall With Experts Smartybro
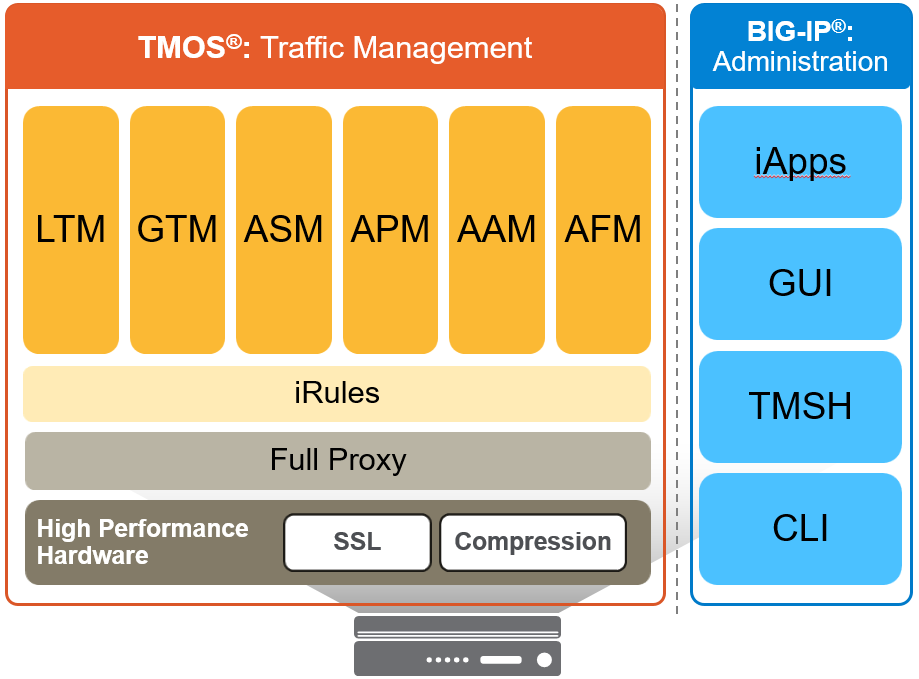
F5 Ca Application Delivery Fundamentals F5 Solutions And Technology Edgoad Com

Wednesday Webinars 07 22 Advanced Waf Vs Asm And The Benefits Of Advanced Waf Up To 15 1 Youtube

How F5 Networks Application Delivery Controllers Contribute To Gdpr
F5 Big Ip Asm Waf Rules Report Acunetix

Generating F5 Big Ip Application Security Manager Waf Rules From Netsparker Standard Netsparker
Exercise 1 1 Policy Creation
Integrating Opswat Metadefender With F5 Advanced Waf Big Ip Asm Devcentral
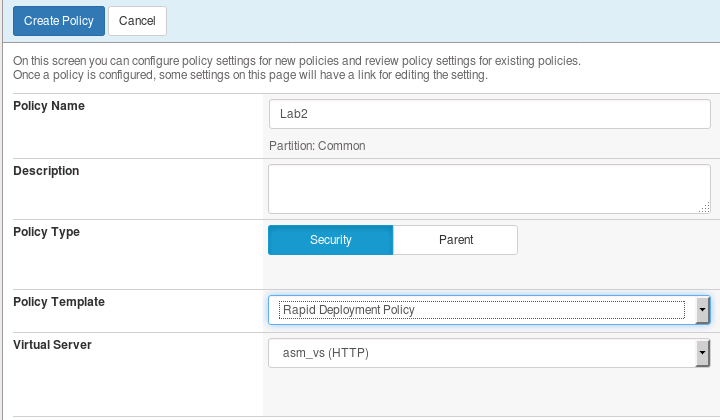
Lab 2 1 User Session Tracking